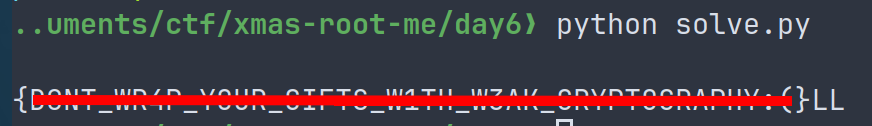
Xmas-Rootme - (06) Unwrap the gift
25/12/2024Today a pretty easy crypto chall.
Today a pretty easy crypto chall.
Source file : sources
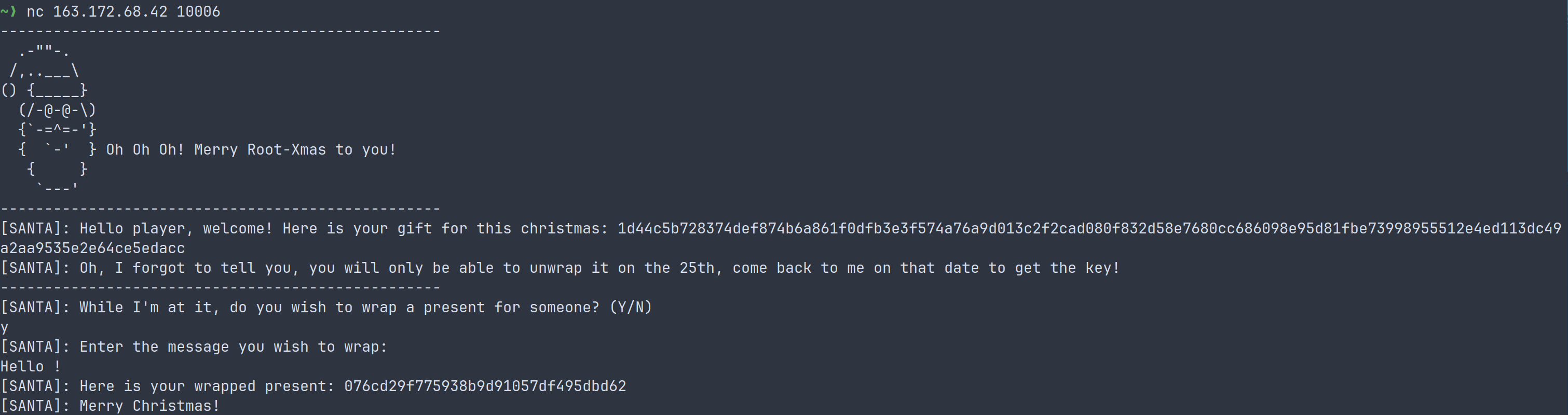
As we can see, we get the encrypted flag, but Santa will only give us the key on the 25th 😢.
But we can give him any text to encrypt (with the same key and iv as we can see on the source code) and get the encrypted result. This sounds like a plaintext attack. When reading the source code we can see that it is using AES in CTR mode.
Reading this article seems like xoring the two encrypted texts and the plaintext gives us the other plaintext :
p_1 -> plaintext 1 (flag) p_2 -> plaintext 2 (our text) c_1 -> cipher of plaintext 1 c_2 -> cipher of plaintext 2 CTR mode : c_1 XOR c_2 = p_1 XOR p_2 p_1 = (c_1 XOR c_2) XOR p_2
We just need to get a ciphers of the same size, I just tried with increasing sizes until I found the good size 🥸.

Then we make a quick program to xor everything.
clear_1 = "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA" cipher_1 = 0xf8f9720c5dc0e159fc6ba524f615a7c40d71bfb270375e70ab74ec1931439c6985f9278e8dd8df78143d2f00c5d1548633ec280de10f18641caca114cf2acadb cipher_2 = 0xebf548092ccff447ea78d035e80da9d01e6fb9ba77224c6ebd04f9102f55ee698fe7259d95c9ca76122e2f11ccc92fef0fa26643af41562a52e2ef5a8164c7d6 xor_1 = (cipher_1 ^ cipher_2) ^ int(clear_1.encode("utf-8").hex(), 16) print(bytes.fromhex(hex(xor_1)[2:]).decode('utf-8'))
And we (almost) get the flag. For some reason I don't have RM in front. But since we know the structure of the flag I dont need it 🤓.